How Builder.ai helped Shoto Inc. gain more visibility with AWS and provided them enhanced continuous security?
Client: Shoto
After starting with a third-party, cloud platform as a service, Shoto decided to switch to Amazon Web Services (AWS) because it offered greater flexibility and better integration across Shoto’s deployment stack. However with this improved visibility and performance gain, Shoto had to rethink their security strategies to safeguard their applications from any unauthorised, unwanted access. This was also important since they were storing users private photos which required enhanced security which should be realtime and automated.
Business challenges
Delivering a fast, simple, and private photo-sharing experience was the goal at Shoto, but in the early days, when things went wrong with various security issues and attempted compromise attempts. They just had basic security group setup but no audit or security standards defined or compiled with. This made them lack in-terms of industry standards for a private photo-sharing application.
Customer requirements
- Enhanced continuous security
- CIS Compliance
- Auditing Capabilities
- Proactive notification of security events
Environment
Shoto runs 30 hosts primarily using Amazon Elastic Compute Cloud. Its deployment stack includes Ruby on Rails, MongoDB, and Redis. The company also relies on Amazon Simple Storage Service for storing photos.
Solution
In order to ensure continuous enhanced security compliance we used the following main tools :-
For monitoring resources and checking compliance:
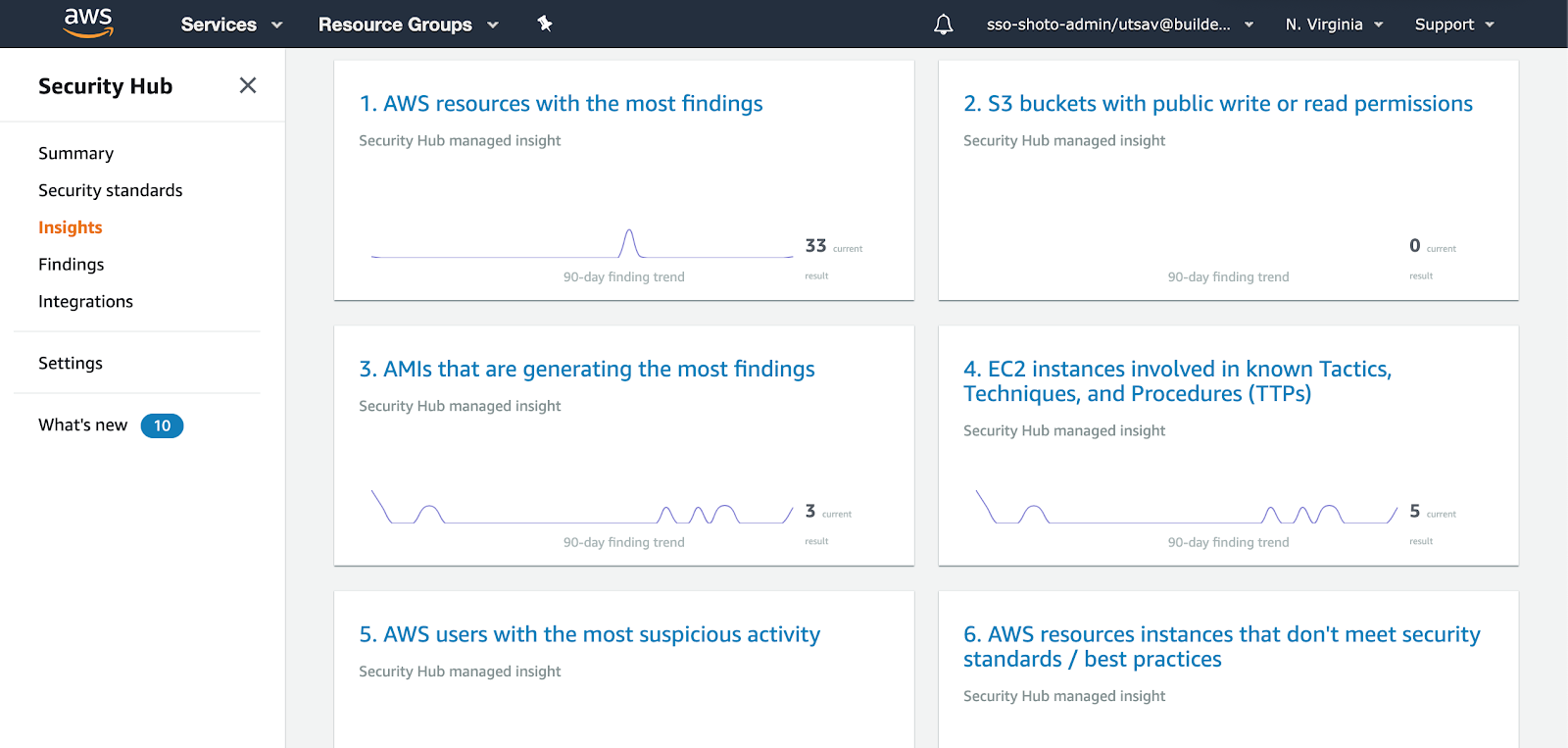
- AWS Security Hub
- AWS Cloudtrail
- AWS Config
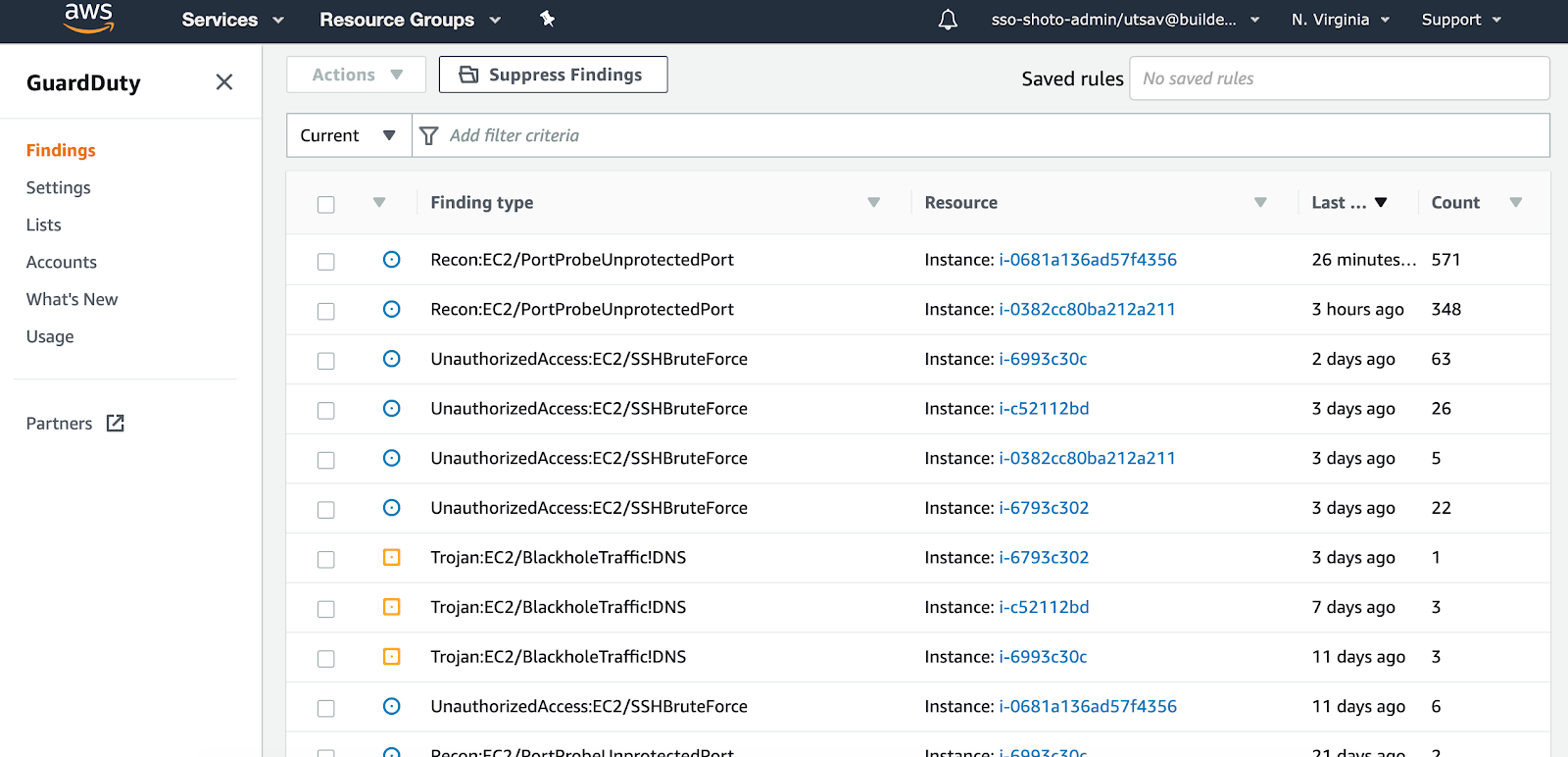
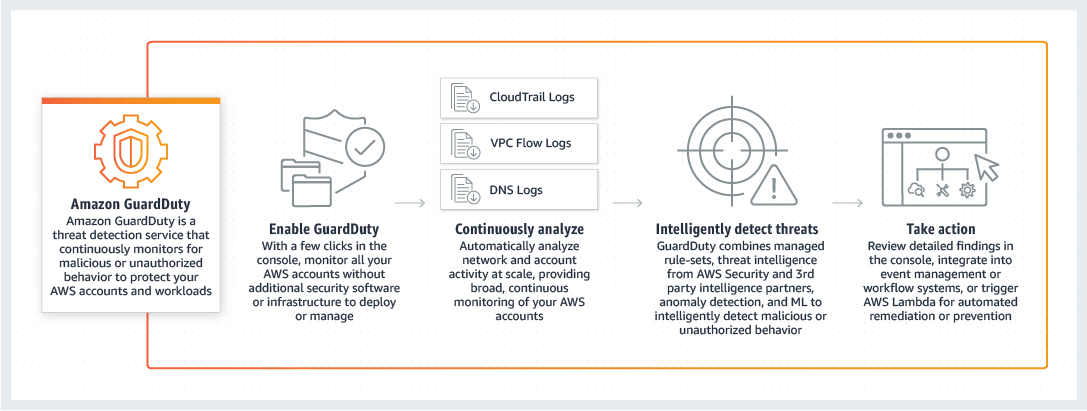
- AWS Guard Duty
For triggering notifications when resources stop being complaint or configuration changes:
- AWS CloudWatch and SNS
For Storage of the logs for historical analysis:
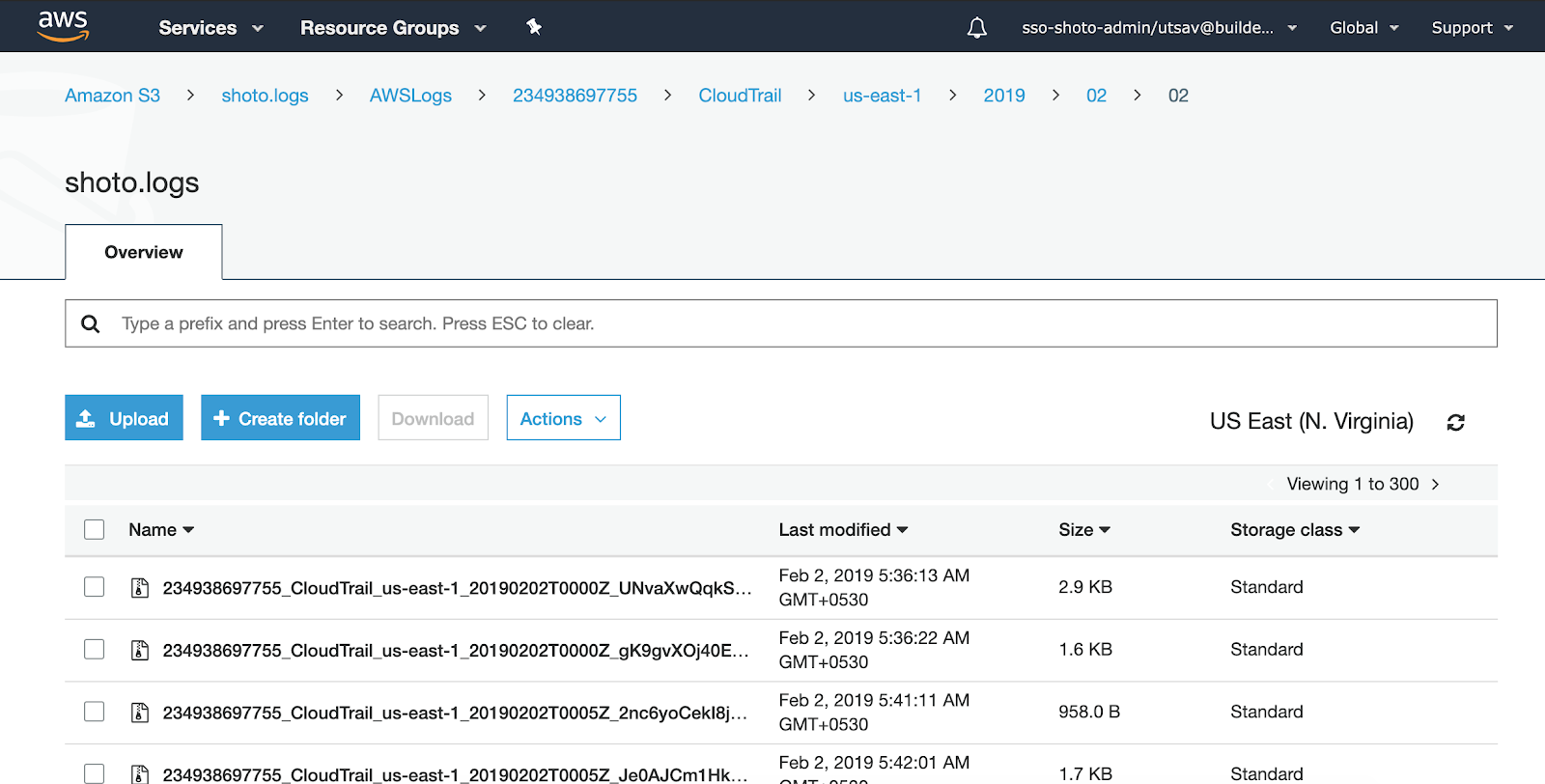
- AWS S3 Standard
Compliance is checked periodically, at least every 24 hours.
For providing enhanced security to the instances we used AWS KMS service to encrypt the databases at rest. Along with that we switched to IAM roles to ensure that instances could run AWS services on behalf of the user.
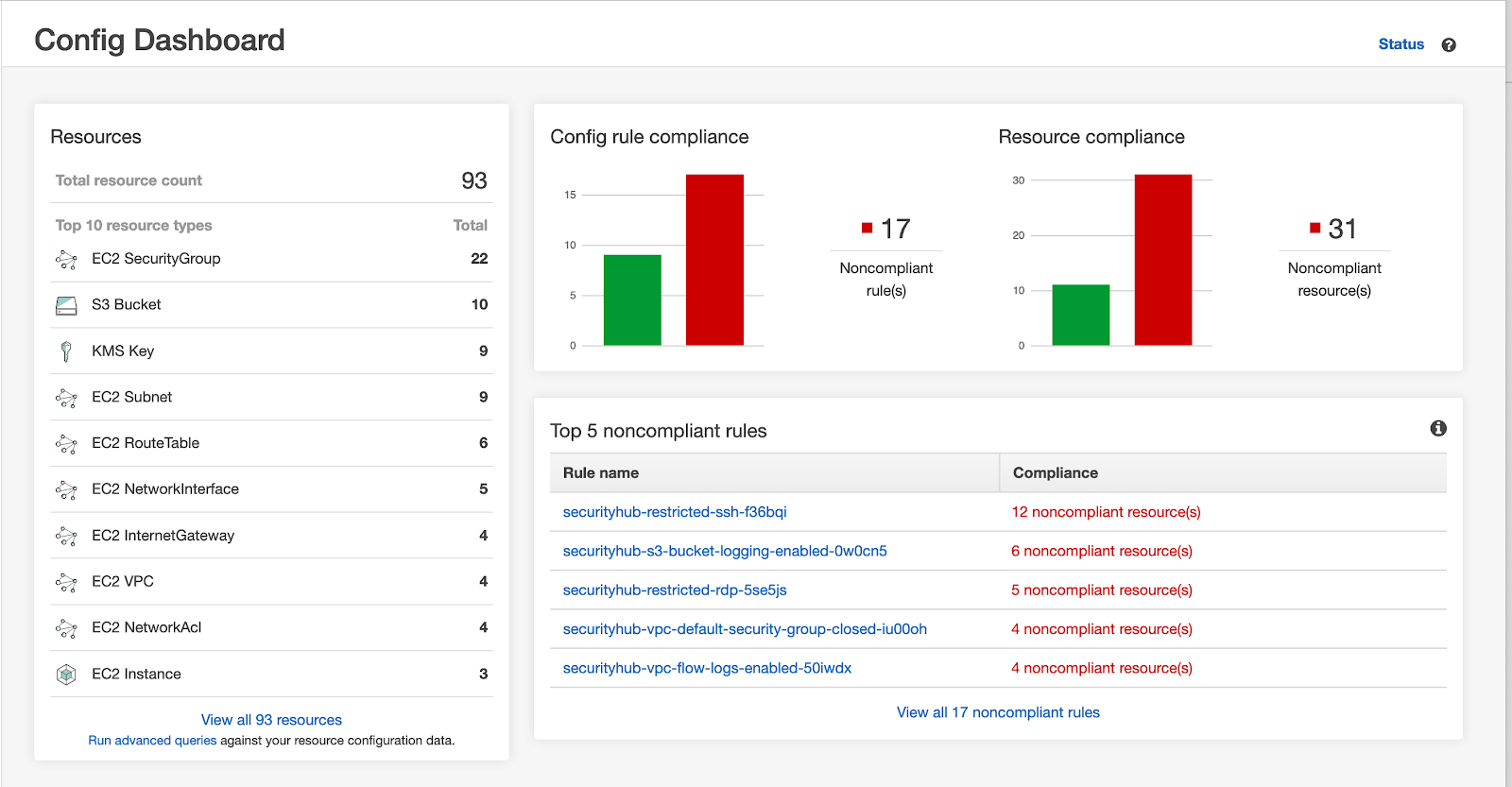
Business Outcome:
Enhanced Continuous Security:This was achieved by utilising AWS Guard Duty, which continuously scanned all logs and provided a collective findings in 1 central dashboard, making it easier to manage and action on. All logs as a matter of process were stored in AWS S3.
CIS Compliance :This was achieved by utilising AWS Security hub, which gives a comprehensive view of the high-priority security alerts and compliance status.
Auditing Capabilities:This was achieved utilising AWS Config which enables Shoto Team to assess, audit, and evaluate the configurations.
Stories published by the editorial team at Builder.ai.










 Facebook
Facebook X
X LinkedIn
LinkedIn YouTube
YouTube Instagram
Instagram RSS
RSS


